As of LCOS 10.70, LCOS supports VPN two-factor authentication (EAP-OTP) with the LANCOM Advanced VPN Client. For this purpose, the internal RADIUS server can manage OTP users.
In addition to his normal VPN user name and password (EAP-MSCHAPv2), the VPN user has an authenticator app, e.g., on his smartphone, on which a second factor is generated and used in addition to the user name / password. Two-factor authentication is only possible with EAP in IKEv2 according to the RFC, so simple PSK or RSA signature methods cannot be used. LCOS supports a vendor-specific implementation together with the LANCOM Advanced VPN Client.
Any apps can be used as authenticators, e.g. from Google, Microsoft or NCP. You can find these apps in the app store of your mobile device.
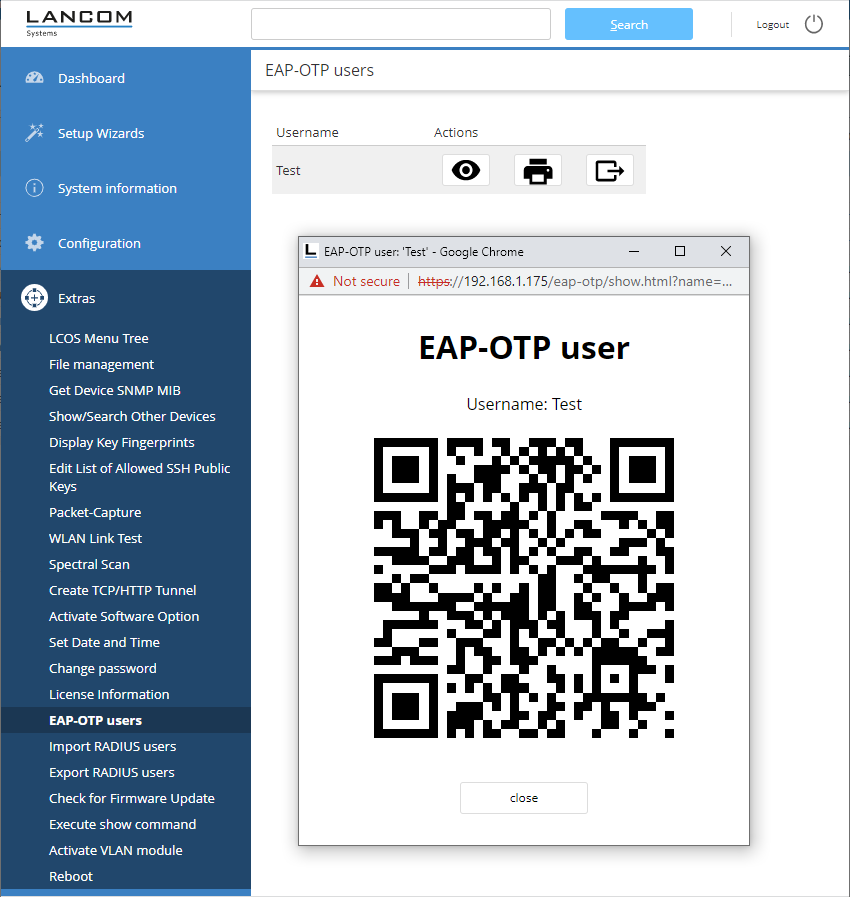
The setup procedure is as follows: First, EAP-VPN with IKEv2 must be configured in the LANCOM device. The internal RADIUS server with its user accounts is used for this purpose. In addition to a RADIUS user account, an OTP user must be created. Subsequently, a QR code can be retrieved in WEBConfig under , which must be scanned by the Authenticator app. This QR code applies per user and must be used each time an Authenticator app is to be set up. WEBconfig generates a QR code per user from the parameters of the OTP user accounts table that can be scanned by Authenticator apps. Alternatively, the key can be added manually in most apps.
Instructions for setting up the entire scenario can be found in the LANCOM Support Knowledge Base.
