Note: The user needs the appropriate access rights to create, select, modify and assign profiles.
In LANconfig, profiles are created under .
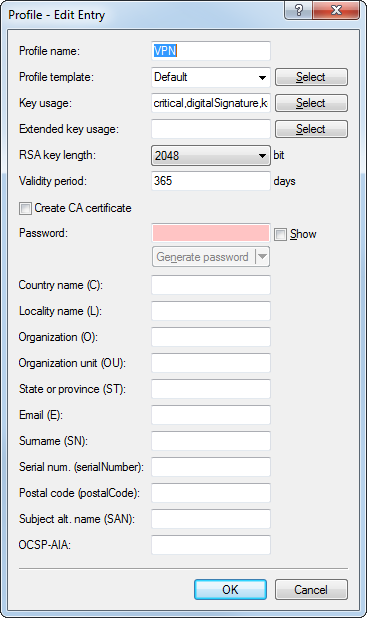
Note: By default three profiles are already available for common application scenarios.
- Profile name
- The unique name of the profile.
- Profile template
- Select a suitable profile template here, if applicable. The profile template specifies which certificate information is mandatory and which can be changed. Templates are created under .
- Key usage
- Specifies for which application the profile is to be used. The following usages are available using the Select button:
Table 1. The available key usages Value Meaning critical This restriction requires the extended key usage to be considered. If the extension is not supported, the certificate is rejected as invalid. digitalSignature Is this option is used, the public key is used for digital signatures. nonRepudiation With this option set, the key is used for digital signatures of a non-repudiation service, i.e. one with a rather long-term character such as notary public service. keyEncipherment If this option is set, the key is used for encrypting other keys or security information. It is possible to restrict the use of encipher only and decipher only. dataEncipherment If this option is set, the key is used for encrypting user data (but not other keys). keyAgreement If this option is used, the "Diffie-Hellman" algorithm is used for key agreement. keyCertSign If this option is set, the key is applied to certificates for signature verification. This is useful for CA certificates, for example. cRLSign If this option is set, the key is applied to CRLs for signature verification. This is useful for CA certificates, for example. encipherOnly This is only useful with the Diffie-Hellman keyAgreement. decipherOnly This is only useful with the Diffie-Hellman keyAgreement. Note: Multiple comma-separated entries can be selected. - Ext. key usage
- Specifies the extended application for which the profile is to be used. The following usages are available using the Select button:
Table 2. Extended usages Value Meaning critical serverAuth SSL/TLS Web server authentication clientAuth SSL/TLS Web client authentication codeSigning Signing of program code emailProtection E-mail protection (S/MIME) timeStamping Furnishing data with reliable time stamps msCodeInd Microsoft Individual Code Signing (authenticode) msCodeCom Microsoft Commercial Code Signing (authenticode) msCTLSign Microsoft Trust List Signing msSGC Microsoft Server Gated Crypto msEFS Microsoft Encrypted File System nsSGC Netscape Server Gated Crypto Note: Multiple comma-separated entries can be selected. - RSA key length
- Sets the length of the key.
- Validity period
- Specifies the duration, in days, for which the key is valid. After this period, the key becomes invalid unless the user renews it.
- Create CA certificate
- Indicates whether this is a CA certificate.
- Password
- Password to protect the PKCS12 certificate file.
The following input creates a certificate ID. The following options are available:
- Country code (C)
- Enter the country identifier (e.g. "DE" for Germany). This entry appears in the subject or issuer of the certificate under C= (Country).
- Locality name (L)
- Enter the name of the locality. This entry appears in the subject or issuer of the certificate under L= (Locality).
- Organization (O)
- Specify the organization that issues the certificate. This entry appears in the subject or issuer of the certificate under O= (Organization).
- Organization unit (OU)
- Specify the unit within the organization that issues the certificate. This entry appears in the subject or issuer of the certificate under OU= (Organization Unit).
- State or province (ST)
- Enter the State or province. This entry appears in the subject or issuer of the certificate under ST= (STate).
- E-mail (E)
- Enter an e-mail address: This entry appears in the subject or issuer of the certificate under emailAddress=.
- Surname (SN)
- Enter a surname. This entry appears in the subject or issuer of the certificate under SN= (SurName).
- Serial no. (serialNumber)
- Enter a serial number. This entry appears in the certificate under serialNumber=.
- Postal code (postalCode)
- Enter the location post code. This entry appears in the subject or issuer of the certificate under postalCode=.
- Subject alt. name (SAN)
- The "Subject Alternative Name" (SAN) links additional data with this certificate. The following data are allowed:
- E-mail addresses
- IPv4 or IPv6 addresses
- URIs
- DNS names
- Directory names
- Any names
- OCSP-AIA
- This field is required for the OCSP server. It contains the name or IP address where OCSP clients can reach the OCSP server. See OCSP server.
Note: The certificate issuer assigns the general name "CN". The "CN" is required as a minimum.
